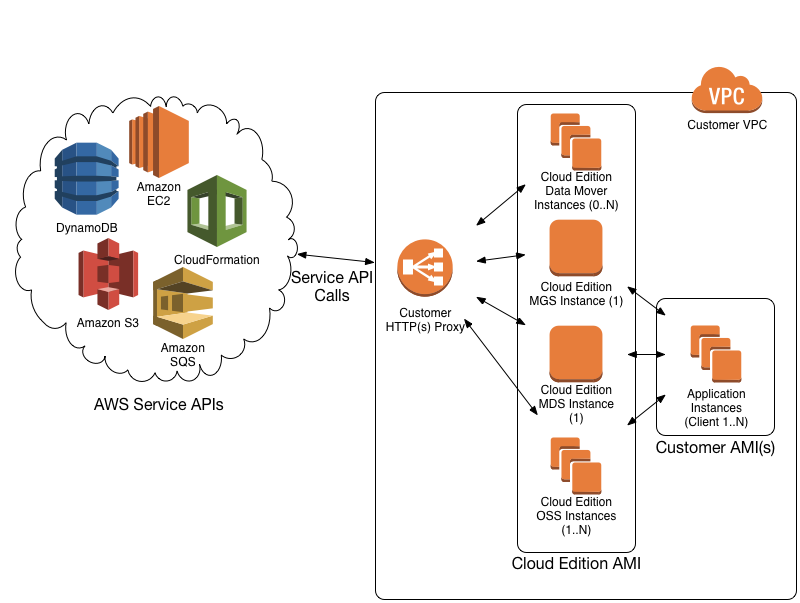
Access to AWS API endpoints
Intel Cloud Edition for Lustre requires access to certain AWS APIs in order to perform initial filesystem configuration as well as to automatically respond to failures in order to maintain High Availability (HA) access to the filesystem. Cloud Edition instances do not require access to the public Internet at large, nor do they require any inbound access other than responses from the AWS API endpoints. Regardless of the connection method, all AWS API traffic is SSL-encrypted.
Lustre filesystem traffic (i.e. connections between Lustre client instances and Cloud Edition server instances) is completely local to the VPC and does not require any outbound connectivity.
For more information about how HA works in Cloud Edition, please refer to the following document: Cloud Edition Documentation - HA and Failover.
Access via NAT Gateway Instance
The default configuration for Cloud Edition creates a NAT instance in a public subnet (i.e. a subnet which has been configured with an Internet Gateway and allows outbound access from instances in that subnet) and uses that gateway to access the AWS API endpoints directly. The gateway instance can also be used as an inbound "jump node" to allow SSH access from outside the VPC. The advantage to this configuration is that it is convenient for testing and "kicking the tires", but may not meet site security requirements.
Access via Managed NAT Gateway (TBD, Future Feature)
Similarly to the NAT Gateway Instance, this option configures an outbound NAT Gateway which enables Internet access for Cloud Edition instances, but does not allow inbound SSH access.
Access via HTTPS Proxy
This configuration for Cloud Edition uses a slightly different CloudFormation template to configure an installation which does not use a NAT Gateway for access to the AWS API endpoints. Instead, a HTTPS proxy address and port may be supplied via the template, and these settings are applied to Cloud Edition instances as they are initialized. The instances will route all of their AWS API traffic via the proxy, which may make this configuration best suited for more restricted environments. Cloud Edition does not currently support HTTPS Proxies which require authentication.
AWS Endpoints Used By Cloud Edition
As of Cloud Edition 1.3, access to the following AWS Endpoints is required for proper functioning of the product. For illustrative purposes, the current us-east-1 endpoint URL is listed, but these endpoint URLs will vary by region and may change over time.
| Service Name | us-east-1 endpoint URL |
|---|---|
| CloudFormation Custom Resource | cloudformation-custom-resource-response-useast1.s3.amazonaws.com:443 |
| CloudFormation Wait Condition | cloudformation-waitcondition-us-east-1.s3.amazonaws.com:443 |
| CloudFormation | cloudformation.us-east-1.amazonaws.com:443 |
| DynamoDB | dynamodb.us-east-1.amazonaws.com:443 |
| EC2 | ec2.us-east-1.amazonaws.com:443 |
| SQS | queue.amazonaws.com:443 |
| S3 (Optional, only required for import) | s3.amazonaws.com:443 |
Encryption
AWS APIs
Cloud Edition uses SSL to protect connections to AWS API endpoints. This protection is built into the underlying AWS SDKs used by Cloud Edition for access to the APIs.
Lustre
A Cloud Edition filesystem may be optionally configured to protect inter-component (servers, clients) Lustre communication via IPSec. This option provides "in flight" data protection. As of version 1.3, EBS Encryption is always enabled to provide "at rest" data protection, as performance testing has shown that there is no performance difference between encrypted and unencrypted EBS volumes.
Please note that IPSec encryption of Lustre communications is CPU-intensive and will have a negative impact on overall Lustre filesystem performance. The amount of impact depends on instance type. Newer instance types based on the Xeon v3 (Haswell) platform perform much better than older instance types due to hardware acceleration for some encryption operations. Please refer to the AWS EC2 Instance Types page for current details.
Intel strongly recommends that customers wishing to enable IPSec encryption for their Cloud Edition filesystems should evaluate the performance/benefit tradeoffs before going into production.